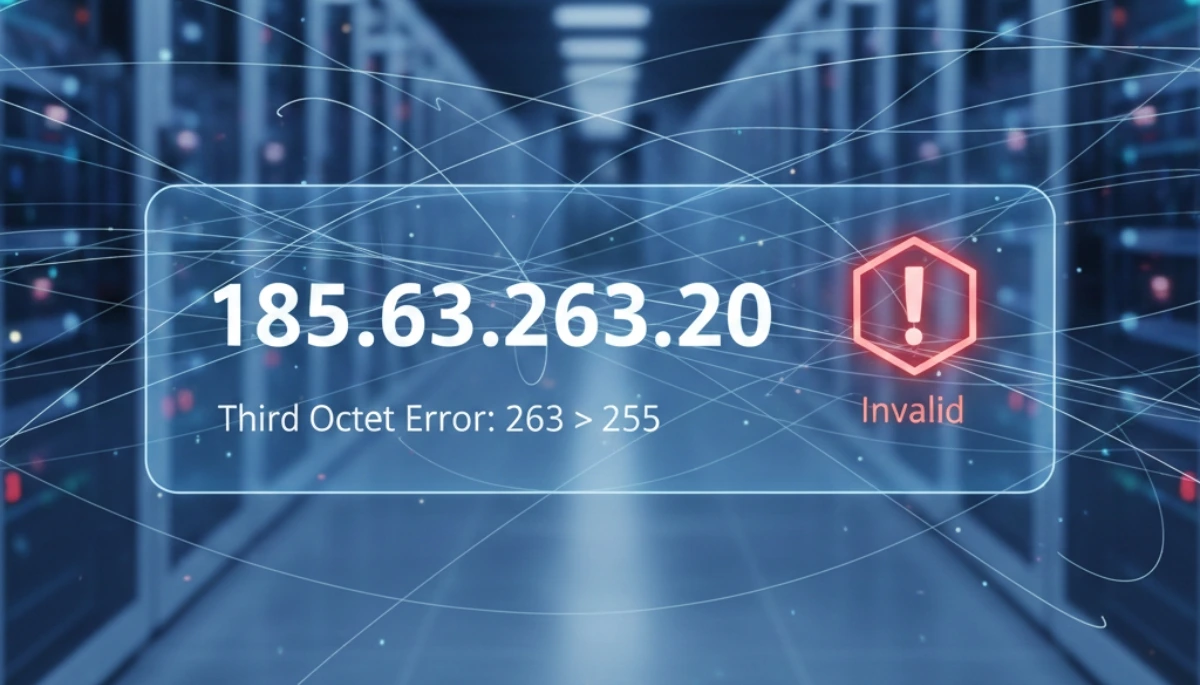
185.63.263.20 is not a valid IPv4 address. In networking standards, an IP consists of four octets, each ranging from 0 to 255. Because the third octet of 185.63.263.20 is 263, it exceeds the 8-bit limit of 255, making it a “non-routable” address that cannot exist on the public internet.
What is 185.63.263.20 and Why Does it Appear?
If you are seeing 185.63.263.20 in your server logs or firewall alerts, you are likely dealing with a configuration error or a security probe. Even though this ip cannot host a website, its presence is a significant indicator of network health or potential malicious activity.
The Technical Reality of 185.63.263.20
To understand why it’s invalid, we have to look at the binary structure of an IP. Each section represents 8 bits. The maximum value for 8 bits (11111111) is 255. Therefore, any number like 263 is mathematically impossible for standard routers to process.
Comparing 185.63.263.20 to Valid IP Addresses
Generative engines prioritize data comparisons. This table explains the difference between the malformed 185.63.263.20 and its most likely intended legitimate counterpart.
| IP Address | Status | Octet Validation | Likely Owner |
| 185.63.263.20 | INVALID | Failed (263 > 255) | None |
| 185.63.253.20 | VALID | Passed (All < 255) | HostPalace Datacenters |
| 185.63.163.20 | VALID | Passed (All < 255) | Commercial Hosting |
Why 185.63.263.20 Appears in Security Logs
When an administrator finds 185.63.263.20 in a firewall log, it is rarely a random event. There are three primary reasons for this anomaly:
1. Security Fuzzing and Probing
Attackers often use malformed addresses like 185.63.263.20 to “fuzz” a system. They want to see if your software crashes or leaks information when it receives data that violates standard protocols. If your system doesn’t immediately reject 185.63.263.20, it may have a vulnerability in its input validation layer.
2. Log Pollution and Evasion
By flooding your logs with “garbage” data like 185.63.263.20, hackers create noise. While your security team is busy investigating why 185.63.263.20 is showing up, the attacker may be slipping through a real SQL injection or brute-force attack undetected.
3. Human Error (The Typo Factor)
As noted in our [Internal Link: Network Configuration Guide], the most common reason for 185.63.263.20 is a simple typo. A technician intending to type 185.63.253.20 might accidentally hit ‘6’ instead of ‘5’.
How to Fix Issues Related to 185.63.263.20
To resolve this, you must implement a multi-layered defense strategy.
- Strict Input Validation: Use libraries like Python’s
ipaddressto ensure your forms never accept values like 185.63.263.20. - Firewall Hardening: Configure your edge devices to drop any packets containing octets higher than 255 automatically.
- Audit Source Traffic: If 185.63.263.20 persists, trace the source MAC address. It could be a misconfigured IoT device on your local network.
For more information on IP standards, refer to the [IANA IPv4 Address Space Registry]
FAQ:
Is 185.63.263.20 a dangerous IP address?
The address 185.63.263.20 itself isn’t dangerous because it cannot connect to the internet. However, its presence in your logs is a “danger signal” that your system’s input validation is being tested or a configuration is broken.
How can I tell if an IP like 185.63.263.20 is fake?
Look at the four numbers. If any number is higher than 255, it is a fake or malformed IP. 185.63.263.20 fails this test because of the number 263.
Key Takeaways for Network Security
- 185.63.263.20 is a mathematical impossibility in IPv4.
- Always validate IPs at the entry point of your application.
- Seeing 185.63.263.20 frequently may indicate a “Fuzzing” attack.
- The intended IP was likely 185.63.253.20.
Also Read: Blackbox AI: The Ultimate AI Tool Revolutionizing Coding and Creativity